AI AppSec that's all signal and no noise
Secure your code from the start with the fastest and most accurate AI-powered appsec tool available. Then get back to work building great apps.
Try it for free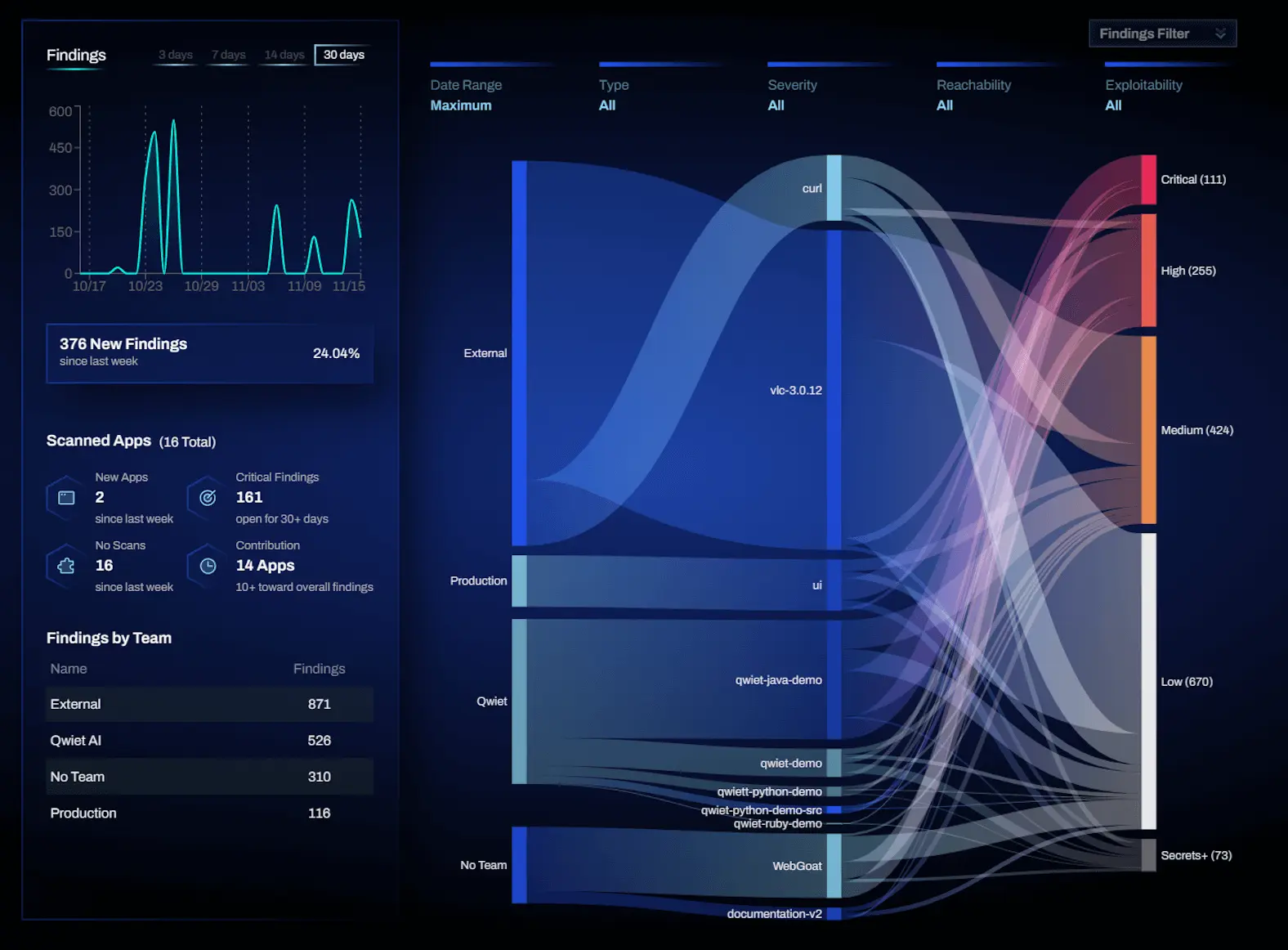
Leading brands trust Qwiet AI

Build secure software faster
Qwiet AI swiftly scans your entire codebase within minutes. Leveraging AI and our patented code property graph scanning method, you can identify vulnerabilities and prioritize them based on severity, reachability, and exploitability. This ensures your team minimizes time spent on addressing false positives and maximizes time dedicated to building outstanding applications.
Play Video
All of your appsec in a single scan
Contextual SCA
Find critical, reachable, and exploitable vulnerabilities across all your OSS libraries
AI
Custom AI trained on 78 billion lines of analyzed code combined with enhanced visibility and insights from the code property graph
Code Property Graph
CPG provides unparalleled visibility into your code and application's dataflow - providing critical data on reachability of vulnerabilities
Integrations
Qwiet AI meets you where you work with integrations into the most popular developer or security tools
See It In Action
What's in it for...
AppSec
Improved vulnerability insights make security a more effective partner for development teams. By highlighting reachable and actively exploited vulnerabilities that could result in costly post-release patches, collaboration with development becomes strategic and productive.
Engineering
Qwiet AI was designed with the developer experience in mind. Faster scan times and prioritized, accurate results mean you spend less time waiting for scans to complete and chasing false positives, and more time building high quality, secure applications.
Your Business
Protect your reputation, bottom line, and customer loyalty from potential threats. Qwiet AI emphasizes preventive security measures, saving your business from the costly aftermath of breaches and positioning it to thrive by prioritizing security from the start
What our customers are saying
Retail
Industry
5 stars out of 5
As a security engineer working with the Dev teams to implement SDLC and Code security standards and compliance, deploying Qwiet AI for static code testing was a great experience. I enjoyed working with the experts from the Qwiet AI team.
Company Size: 500M-1B USD
Healthcare & Biotech
5 stars out of 5
We are able to scan our apps more often with the platform because its fast enough to fit into our SDLC process.
Company Size: 500M-1B USD
Healthcare & Biotech
5 stars out of 5
Significant realization of operational goals to reduce time of issue discovery to resolution, allowing the app dev teams to stay focused on the production and delivery of high business value products and services versus the older cultural approach of… hunting large quantities of bugs and flaws as the KPI measuring success.
Company Size: 500M-1B USD
The Qwiet Blog
-
What are the limitations of using ChatGPT to write code?
April 22, 2024 | 6 min
Love them or hate them, large language models (LLM) are here to stay. After opening the Pandora’s Box of ChatGPT in late 2022, everyone from developers to grandmas began using the tool to get the answers they wanted – and fast. As with every other new technology, ChatGPT created a new set of security risks, […]
Read more
-
Why Is Vulnerability Remediation Hard?
April 17, 2024 | 5 min
Imagine yourself standing in a local fair at night. The bright lights from the games beckon you, and you see your favorite game, the one you’re best at – Whack-A-Mole. You excitedly walk up to the booth, plunk down your few dollars, and get ready to whack a bunch of plastic, animatronic moles back into […]
Read more
-
AppSec 101 – Dependency Management
April 9, 2024 | 7 min
Introduction In the world of software development, managing dependencies is like keeping the gears of a well-oiled machine running smoothly. Get ready to dive deep into practical strategies and tools that streamline your development process, ensuring your projects are as efficient and error-free as possible. This is your guide to mastering dependency management, making every […]
Read more
-
AppSec 101 – Error Handling and Logging
April 9, 2024 | 8 min
Introduction Have you ever wondered why meticulously coded applications sometimes falter or how the unseen processes within can impact user experience? This article dives into error handling and logging—essential practices that ensure software resilience, security, and maintainability. You’ll learn the significance of these components, understand their implementation, and discover tools that fortify application development. What […]
Read more

