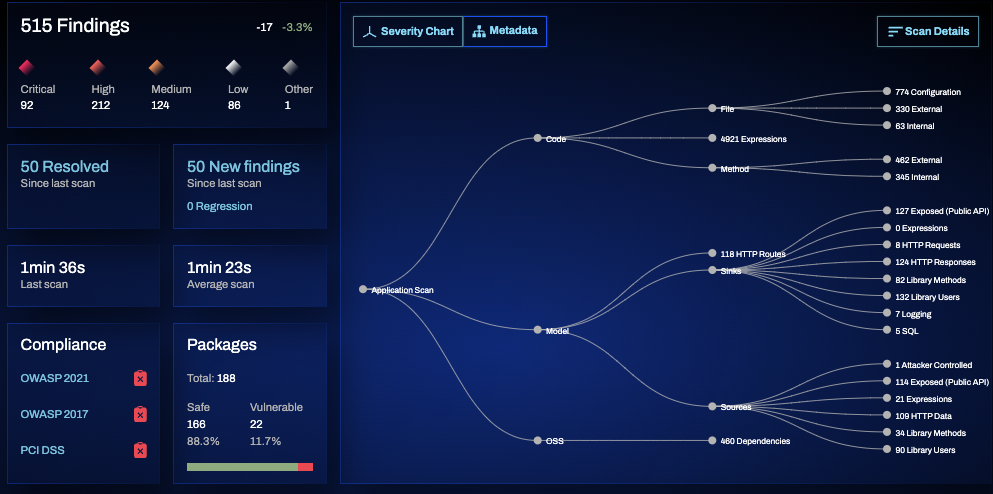
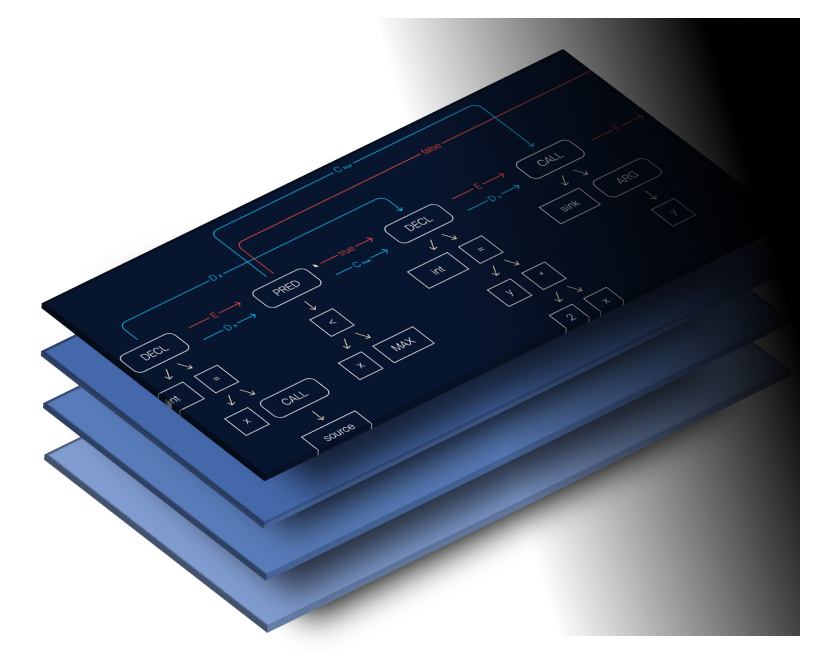
Code Property Graph
Our patented CPG delivers unrivaled speed and accuracy to detect vulnerabilities
Extensible
Code Analysis
Unique
Data Flow
Tracker
The Code Property Graph (CPG) breaks down code into its fundamental components, identifying functional elements and data flow paths into a single property graph. This allows preZero a holistic view of code being scanned, looking at not just the elements of the application, but also analyzing how data is flowing and how libraries interact with each other. This provides a much more accurate method for detecting security issues quickly and with dramatically lower false positives.
CPG Enhanced by AI
By applying AI and ML to the CPG, preZero becomes even more powerful and effective at finding zero-day and pre-zero-day vulnerabilities in code. Previously undiscovered vulnerabilities, which could take days and potentially weeks of analysis by security analysts and/or code scientists to discover, can be uncovered in a matter of seconds through the application of AI and ML analysis of an application’s CPG.
Once results are analyzed by preZero and verified by Qwiet’s data science team, they are then fed back into the ML models, to produce even quicker discovery on the next scan, allowing the power and efficacy of the AI to continue to grow.

What Does This
Mean For Me?
Deeper Visibility,
Deeper Insight into
Your Data Flow
Where do the vulnerabilities lie? And what other elements of the app are affected? The Code Property Graph (CPG) shows you by mapping the data flows throughout your entire application and calls out what’s subject to attack.
Across user inputs, log files, databases, custom code, open-source libraries, SDKs, APIs, and microservices, the graph detects dependencies and identifies control flows, and the data lifecycle–all queryable.
The CPG is a breakthrough innovation in static code analysis that allows the preZero platform to quickly analyze code and pinpoint the attackable vulnerabilities, enabling organizations to prioritize the fixes that will have the biggest impact to the security of your application.
To read more about the math behind the CPG and how it is used to detect vulnerabilities in code quickly and accurately, please see the paper co-authored by Qwiet’s very own Fabian Yamaguchi.
Utilizing the speed and efficiency of the CPG, Qwiet customers performed, on average over a year, one scan of their entire source code a day for a 1 minute 30 seconds per scan.
